By Scott Stuewe, DirectTrust President and CEO
What makes us what we are? Who knows who we are?
If you had to prove you are who you say, for the very first time, if you don’t have an ID already, how would you do it?
My mother was there when I was born and could tell you it’s me, but she is no longer with us. What I have from that moment when I came into the world is a birth certificate – just a piece of paper – that is evidence of where I was born, and to whom, and when the blessed event occurred. But does it really tell you I am that person?
The best we can do (in the absence of my mother, who besides her doctor and nurses was the only one there at my birth) is to be reasonably assured that I am me.
Don’t worry, I’m not having an identity crisis, just making a point. Given only the ways we can do it today, proving identity is hard.
Hard or not, identity-proofing is the first step in establishing trust for healthcare data exchange. Without it, security is impossible to ensure.
To create an identity-proofing process that is “trustworthy”, in addition to just working reliably, it needs to be secure, repeatable, auditable, transparent, and independent. Those operating under the process will evaluate and safeguard identity-evidence, (artifacts representing true and verifiable facts about individuals according to published standards) in order to assure the identity of individuals and their linkage to a living human person. The organizations that do this process at scale today are referred to as “registration authorities”. DirectTrust accredits such organizations that support our network.

Popeye famously said “I YAM WHAT I YAM…” in a much simpler time when most of us were moving through the world anonymously unless we were famous (or infamous).
Back in the day, there was a reasonable assumption that nobody knew (or perhaps even cared) about the trivial, yet true (and unchangeable), facts about us. In the internet age, we are also identified by what we do and buy, where we go and who we know. And a great deal of this data is available, either for free or for sale. You can find my mother’s maiden name on the web in one good search if you know my name and that she has passed on. Even trivial facts that I gave my bank like “the best man at my wedding” or “my first dog” have likely been stolen in the 135 million records compromised in the September 2017 Equifax Data Breach.
 In these days of social distancing, Facebook surveys encouraging users to “post a picture of your first car” are inviting people to make public the very type of information that frequently is used to control or verify access to bank accounts, including mine. While my data may have been compromised in the Equifax breach, at least I haven’t fallen victim to posting a picture of my first car on the web for all to see, so there is that comfort.
In these days of social distancing, Facebook surveys encouraging users to “post a picture of your first car” are inviting people to make public the very type of information that frequently is used to control or verify access to bank accounts, including mine. While my data may have been compromised in the Equifax breach, at least I haven’t fallen victim to posting a picture of my first car on the web for all to see, so there is that comfort.
Because more of the true facts about a person are no longer reasonably expected to be private, the process of ensuring a person is who they say they are has gotten a lot harder.
This is important for DirectTrust as our community needs to identity-proof millions of individuals and organizations to ensure trust-in-identity for access to health data. While identity-proofing an organization (a medical practice, health system, insurance company, home care agency or other data exchange participant) is different than id proofing an individual, it always starts with identity-proofing a person, and then ensuring they represent the organization that is the subject of the proofing.
NIST (National Institute for Standards and Technology) issues guidelines for identity-proofing for government entities, and the private sector generally follows these guidelines as well. It used to be an acceptable proof of identity (under NIST 800-63-2) to ask someone for facts assumed only to be known by them in addition to an account a person was in control of and could be validated. This method was referred to as Knowledge Based Authentication and could be done “remotely” and “unsupervised”.
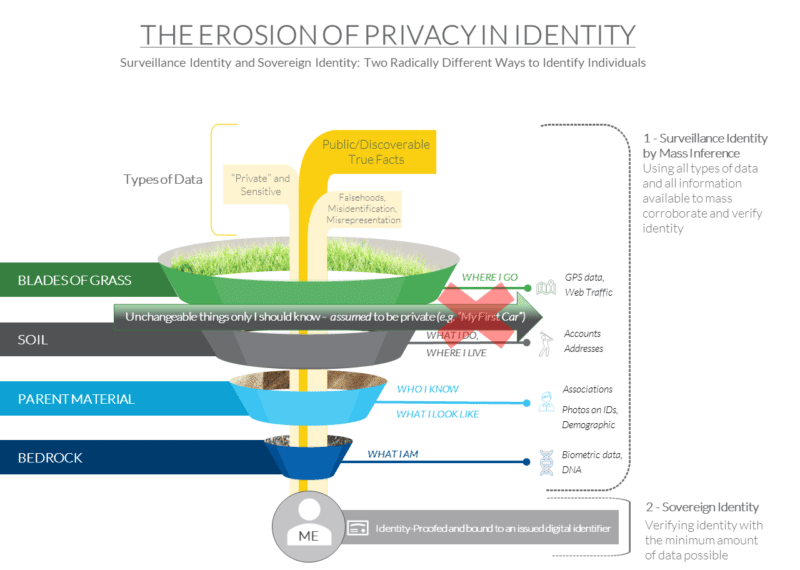 But as more of these true facts are knowable by the general public or by bad actors, much higher bars have been set for identity proofing. The big red “X” in the figure here shows that unchangeable facts about me like “my first car” that I might have provided to get a bank account website credential can no longer be used for identity-proofing.
But as more of these true facts are knowable by the general public or by bad actors, much higher bars have been set for identity proofing. The big red “X” in the figure here shows that unchangeable facts about me like “my first car” that I might have provided to get a bank account website credential can no longer be used for identity-proofing.
The new NIST guidelines (800-63-3) describe a series of approaches for reaching the new identity assurance levels. The new baseline standard for proofing for most purposes is IAL2 (Identity Assurance Level 2) – which is roughly equivalent to the standard utilized for the issuance of the new REAL ID Driver’s license standard and can be conducted either remotely or in-person. If you have a REAL ID and didn’t have a US passport prior, you know how rigorous the process is – depending on what is available as evidence and how “strong” it is it might take three or four different pieces of evidence to complete. If you have TSA pre-check, you have been through an IAL2 in-person process. In fact, if someone can present a valid and verifiable REAL ID or US passport in person and the picture matches their likeness, that will suffice for the purposes of IAL2 proofing. Both REAL IDs and Passports are examples of “superior” evidence of a person’s identity under 800-63-3.
There are also technologies that are beginning to be in use that employ a smartphone camera and software to compare the “live” likeness of an individual to the photo on a REAL ID. In order to support proofing over the web, something like this is certainly needed to replace knowledge-based authentication. So far though (in early 2020), only about 34% of driver’s licenses are REAL ID compliant – 95 of 276 million total Drivers Licenses and IDs. Because of this, most individuals will need to present multiple pieces of evidence in person and perhaps go to a notary to prove their identity. Getting everyone proofed will be costly.
The real problem is that the using a proofed identity in different contexts is not commonly done – you can’t use a REAL ID to log on to your bank for example. People are also worried about the privacy implications of identity assurance. This means our identity is being proofed all the time in these different circumstances, over and over.
Proofing identity is really hard, but really important for trust-in-identity for healthcare exchange in particular. If we need to identity-proof everybody who wants to communicate health records and other sensitive information, how can we do that without unduly increasing the cost of care? Can we be sure enough about these proofed identities to allow for health data to flow?
In the next post in this ongoing series we will examine two approaches to “resolving identity”.
